Strengthen Your Network with FREE Cyber Awareness Training
In today's interconnected world, the need for robust cybersecurity measures is more critical than...

Remote access VPN has long served us well, but the recent increase in remote working has cast a spotlight on the limitations of this aging technology. While some organizations continue to extract every bit of mileage they can from VPN, many are looking for a better alternative – something that addresses the challenges with remote access VPN. Several organizations have already started to fully embrace the next generation of remote access technology: ZTNA or zero trust network access. ZTNA offers better security, more granular control, increased visibility, and a transparent user experience compared to traditional remote access VPN.
In this blog, we will examine the limitations and challenges with traditional remote access VPN and the benefits that zero-trust network access can provide and summarize with a shopping list of critical capabilities you should be looking for in your new ZTNA solution.
Remote access VPN has been a staple of most networks for decades, providing a secure method to remotely access systems and resources on the network. However, it was developed during an era when the corporate network resembled a medieval fortification – the proverbial castle wall and moat that formed a secure perimeter around network resources within. VPN provided the equivalent of a secure gatehouse for authorized users to enter the safe perimeter, but once they were in, they had full access to everything within the perimeter.
.png?width=548&name=MicrosoftTeams-image%20(1).png)
Of course, networks have evolved substantially, being more distributed than ever. Applications and data now live in the cloud, users are working remotely, and networks are under siege by attackers and hackers looking for any weakness to exploit.
Administering a remote access solution based on traditional VPN (IPSec/SSL) in any kind of modern environment can be extremely painful. You have to contend with IP management, traffic flows and routing, firewall access rules, as well as client and certificate deployment and configuration. Anything beyond a few dozen users turns this into an unnecessary full-time job - just to keep this running. If that wasn't enough, security becomes an absolute nightmare to monitor and control.
Remote access VPN does a good job of getting you through the perimeter and onto the corporate network as if you were physically there, but at that point, you’re implicitly trusted and given broad access to the resources on that network which may present unnecessary and enormous security risks.
Remote access VPN has no awareness of the state of the device used to connect to the corporate network, creating a potential conduit for threats to enter the network from devices that may have been compromised.
Remote access VPN provides a single point-of-presence on the network, which will potentially necessitate back hauling of traffic from multiple locations, data centers, or applications through the remote access VPN tunnel.
Remote access VPN is unaware of the traffic and usage patterns it is facilitating making visibility into user activity and application usage more challenging.
Remote access VPN clients are notorious for offering a poor user experience, adding latency or negatively impacting performance, suffering from connectivity issues, and generally being a burden on the help desk.
Remote access VPN clients are difficult to set up, deploy, enroll new users, and decommission departing users. VPN is also challenging to administer on the firewall or gateway side, especially with multiple nodes, firewall access rules, IP management and traffic flows and routing. It quickly becomes a full-time job.
Zero trust network access (ZTNA) has been designed from the start to address the challenges and limitations with remote access VPN, offering a better solution for users anywhere, to connect securely to the applications and data they need to do their jobs, but nothing more. There are a few fundamental differences that set ZTNA apart from remote access VPN. As the name implies, ZTNA is founded on the principles of zero trust – or trust nothing, verify everything. Zero trust essentially eliminates the concept of the old castle wall and moat perimeter in favor of making every user, every device, and every networked application their own perimeter and only interconnecting them after validating credentials, verifying device health, and checking access policy. This dramatically improves security, segmentation, and control.
.png?width=651&name=MicrosoftTeams-image%20(2).png)
Another key difference in how ZTNA works is that users are not just dropped on the network with complete freedom of movement. Instead, individual tunnels are established between the user and the specific gateway for the application they are authorized to access, and nothing more - providing a much more secure level of micro-segmentation. This has a number of benefits for security, control, visibility, efficiency and performance. For example, remote access VPN provides zero insights into which applications users are accessing, while ZTNA can provide real-time status and activity for all your applications proving invaluable in identifying potential issues and performing licensing audits. The added micro-segmentation that ZTNA provides ensures there's no lateral movement of device or user access between resources on the network. Each user, device, and application or resource is literally its own secure perimeter and there's no longer any concept of implicit trust.
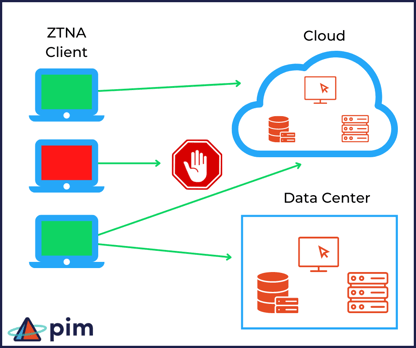
ZTNA is inherently more dynamic and transparent by nature, working in the background without requiring interaction from the user beyond the initial identity validation. This experience can be so smooth and
frictionless that users won’t even realize they are connecting to applications via secure encrypted tunnels.
Zero Trust Network Access offers enormous benefits but is primarily being adopted for one or more of these reasons:
ZTNA solutions are a much easier solution for managing remote access for staff working from home. They make deployment and enrollment easier and more flexible, turning what may have been a full-time job with VPN into something much less resource It's also more transparent and simpler for your staff working remote.
ZTNA solutions provide much better application security with micro-segmentation, the integration of device health into access policies, continuous authentication verification and just the elimination of implicit trust and the lateral movement that comes along with VPN.
ZTNA solutions eliminate a common vector of attack for ransomware and other network infiltration attacks. Since ZTNA users are no longer "on the network", threats that might otherwise get a foothold through VPN have nowhere to go with ZTNA.
ZTNA enables better security and more agility in quickly changing environments with users coming and going. Stand-up new applications quickly and securely, easily enroll or decommission users and devices, and get insights into application status and usage.
ZTNA is founded on the principle of zero trust or “trust nothing, verify everything.” This provides significantly better security and micro-segmentation by effectively treating each user and device like their own perimeter and constantly assessing and verifying identity and health to obtain access to corporate applications and data. Users only have access to applications and data defined explicitly by their policies, reducing lateral movement and the risks that come with it.
ZTNA integrates device compliance and health into access policies, giving you the option to exclude non-compliant, infected, or compromised systems from accessing corporate applications and data and eliminating an important threat vector and reducing risk of data theft or leakage.
ZTNA is network agnostic, able to function equally well and securely from any network be it home, hotel, café, or office. Connection management is secure and transparent regardless of where the user and device are located, making it a seamless experience no matter where the user is working.
ZTNA provides a frictionless, seamless end user experience by automatically establishing secure connections on demand behind the scenes as they are needed. Most users won’t even be aware of the ZTNA solution that is helping protect their data.
Better Visibility
ZTNA can offer increased visibility into application activity that can be important for monitoring application status, capacity planning, and licensing management and auditing.
ZTNA solutions are often much leaner, cleaner, and therefore easier to deploy and manage. They can also be more agile in quickly changing environments with users coming and going - making day-to-day administration a quick and painless task and not a full-time job.
In today's interconnected world, the need for robust cybersecurity measures is more critical than...
When you hire a new employee, there is a lot to think about in terms of getting them all set up on...
