What to do AFTER a Ransomware Attack
Ransomware attacks are as costly as they are common with a suspected attack happening every 11...
As cyber threats increase in volume, complexity, and impact, organizations are increasingly turning to managed detection and response (MDR) services to detect and neutralize advanced attacks that technology solutions alone cannot prevent. In fact, Gartner anticipates that by 2025, 50% of companies will be using MDR for threat monitoring, detection, and response.
However, the proliferation of defense solutions on the market can make it difficult to understand what exactly MDR is, how MDR fits within your wider cybersecurity ecosystem, and the benefits of using an MDR service. This blog post answers these questions and offers practical guidance on what to consider when choosing an MDR service.
To understand the benefits of MDR and what’s behind the growing demand for MDR services, it’s important to understand what MDR is — and what it’s not.
Managed detection and response (MDR) is a fully managed, 24/7 service delivered by experts who specialize in detecting and responding to cyberattacks that technology solutions alone cannot prevent.
MDR should not be confused with EDR (endpoint detection and response) and XDR (extended detection and response). While MDR, EDR, and XDR all support and enable threat hunting, EDR and XDR are tools that enable analysts to hunt for and investigate potential compromise; with MDR analysts hunt for, investigate, and neutralize threats on your behalf.
As their names suggest, EDR tools work with data points from endpoint protection technology, while XDR tools extend their data sources across a wide IT stack (including firewall, email, cloud, and mobile security solutions) to provide greater visibility and insights. At pim, we use Sophos, which utilizes industry-leading EDR and XDR solutions when delivering MDR service as part of our day-to-day cybersecurity management.

All types of organizations across all sectors use MDR services, from small companies with limited IT resources to large enterprises with an in-house security operations (SOC) group. The question is really how do organizations work with MDR services?
At pim, we support all three approaches, adapting to individual customer requirements as needed.
The reality is that technology solutions alone cannot prevent every cyberattack. To avoid detection by cybersecurity solutions, malicious actors increasingly use legitimate IT tools, exploit stolen credentials and access permissions, and leverage unpatched vulnerabilities in their attacks. By emulating authorized users and taking advantage of weaknesses in an organization’s defenses, malicious actors can avoid triggering automated detection technologies.
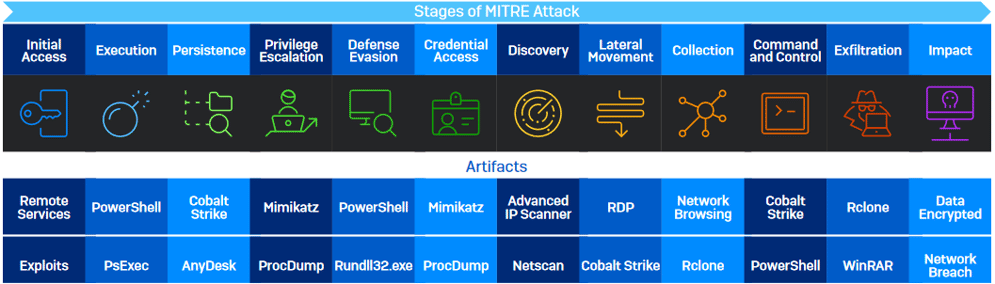
The image below details the top artifacts (tools) used by attackers in each stage of the MITRE ATT&CK chain, as seen by Sophos’ frontline threat hunters in 2021. As you can see, tools used regularly by IT teams such as PowerShell, PsExec and RDP are
frequently abused by adversaries. Automated technologies struggle to differentiate between legitimate IT staff using these tools and attackers exploiting them using stolen credentials.
Stopping these advanced ‘living-off-the-land’ attacks requires a combination of technology and human expertise. Every time an attacker takes an action, it creates a signal. By combining human expertise with powerful protection technologies and advanced AI-powered machine learning models, security analysts can detect, investigate, and neutralize even the most advanced human-led attacks to prevent data breaches.
While threat hunting, investigation, and response can be performed solely in house using EDR and XDR tools, there are extensive benefits to using an MDR service either alongside your in-house team or as a fully outsourced service.
While human-led managed detection and response is an essential layer of cyber defense, high-quality protection technologies remain critical. Endpoint, network, email, and cloud security technologies continue to play a vital role in today’s defenses — and the right solutions can increase the effectiveness and impact of an MDR service:
With that in mind, let’s now look at the top five benefits reported by organizations that use MDR services.
One of the major advantages of using an MDR provider over in-house only security operations programs is elevated protection against ransomware and other advanced cyber threats.
With MDR you benefit from the breadth and depth of experience of pim’s analysts. We will experience a far greater volume and variety of attacks than any individual organization, giving us a level of expertise that is almost impossible to replicate in house.
Our MDR teams also investigate and respond to incidents every day, giving them much greater fluency in using threat hunting tools. This enables us to respond more quickly and accurately at all stages of the process — from identifying the signals that matter to investigating potential incidents and neutralizing malicious activities. Working as part of a large team also enables us to share our knowledge and insights, further accelerating response. The pim and Sophos MDR team collates runbooks for each threat or unique actor that we come across. Once an adversary is identified in the course of an investigation, rather than needing to carry out widespread research at the time of an attack, our team can reference the runbook and then leap straight into action.
The runbooks are continually updated, and analysts record salient information with
every engagement, such as:
 A further advantage of our MDR service is that it can apply intel from one customer to others that match the same target profile, enabling us to proactively prevent similar attacks in that community. Examples of scenarios when our MDR team proactively investigates customers’ estates include:
A further advantage of our MDR service is that it can apply intel from one customer to others that match the same target profile, enabling us to proactively prevent similar attacks in that community. Examples of scenarios when our MDR team proactively investigates customers’ estates include:
Should our analysts detect any suspicious signals, they are able to swiftly investigate and remediate the situation, creating community immunity for the targeted group.
The greater breadth and depth of experience and ability to apply learnings across our clients’ environments enables the pim and Sophos MDR teams to elevate organizations’ defenses above and beyond what they could achieve on their own.
Threat hunting is time consuming and unpredictable. For IT professionals juggling multiple tasks and priorities, it can be hard to keep up with the challenge: 79% of IT teams admit they are not completely on top of reviewing logs to identify suspicious signals or activities.
Given the potential impact of an attack on the organization, when something suspicious is detected, you need to drop everything so the threat can be investigated and acted on immediately. The urgent nature of the work can prevent teams from focusing on more strategic — and often more interesting — challenges.
Working with our MDR service enables you to free up IT capacity to support business- focused initiatives. Organizations using Sophos MDR consistently report considerable IT efficiency gains from using our service, which in turn enables them to better support their organization’s goals.
With bad actors located around the globe, an attack can come at any time. Adversaries are most active at the times when your IT team is least likely to be online, such as evenings, weekends, and holiday periods. Consequently, threat detection and response is a round-the-clock task; if you only do it during office hours, you leave your organization exposed.
By providing 24/7 coverage, MDR services provide considerable reassurance and peace of mind. For IT teams this means quite literally, being able to sleep better at night. They can relax knowing that the buck stops with the MDR provider — not them — and regain their personal time.
For senior leaders and customers, 24/7 expert coverage and a high level of cyber readiness at all times provides powerful reassurance that their data and the organization itself are well protected.
Threat hunting is a highly complex operation. Individuals in this space need to possess a specific and niche set of skills, and the typical traits required of a threat hunter include:
Creative and Curious – Looking for threats can be akin to looking for a needle in a haystack, and threat hunters can often spend days looking for threats, using numerous methods to unearth them.
Experience in Cybersecurity – Threat hunting is one of the most advanced operations within cybersecurity, so prior experience in the field and foundational knowledge are a must.
Threat Landscape Knowledge – Understanding the latest threat trends is essential when seeking out and neutralizing unknown entities.
MDR services provide the expertise for you. At pim and Sophos, we have hundreds of expert analysts that provide continuous MDR services to customers across the globe. Sophos MDR enables customers to expand their security operations capabilities without expanding their headcount.
Maintaining a 24/7 threat hunting team is expensive. To provide round-the-clock coverage, you need a minimum of five or six cybersecurity staff members working separate shifts. MDR services provide a cost-effective way to secure your organization and stretch your cybersecurity budget further.
Plus, by elevating your protection, MDR services also greatly reduce the risk of experiencing a costly data breach and avoid the financial pain of dealing with a major incident. With the average cost of remediating a ransomware attack in mid-sized organizations coming in at $1.4 million in 2021, investing in prevention is a wise financial decision.
MDR services differ from provider to provider. There are many things to consider when evaluating services — be sure to explore the four areas below.
Do you want an MDR vendor to completely manage your threat response, co-manage threat response with your team, or alert your team so it can take action? Identify your preferred level of support and interaction and see how vendors stack up. At pim, we act as an extension of our clients’ IT teams in whichever capacity they need us. From fully managed 24/7 support to quarterbacking an in-house
Broader, deeper experience responding to cyber threats leads to better defenses. Understand the scale of experience that vendor MDR analysts can access and how they apply collective learnings across their customers’ estates. Also, explore the depth of security expertise behind a vendor’s MDR team and the quality of contextual insights provided to help analysts prioritize and investigate
alerts.
Sophos MDR secures over 11,000 organizations across the globe, working across sectors such as healthcare, education, manufacturing, retail, technology, finance, government, services, and many others. This breadth and depth of experience
enables us to deliver unparalleled protection to our customers.
Behind Sophos MDR is the Sophos X-Ops team. With over 30-years’ malware expertise and world-leading AI capabilities, Sophos X-Ops provides deep insights and analysis to help MDR agents quickly identify and neutralize attacks
An effective MDR vendor becomes an extension of your own team — make sure it is a vendor you want to work with once the contract is signed. Speak to existing customers to understand their experiences and check out independent review sites
for customer feedback.
Sophos MDR is the most reviewed and highest rated MDR provider on Gartner Peer Insights as of August 1, 2022, with an average rating of 4.8/5.
Adversaries don’t follow a single technology path — neither should your MDR vendor’s threat hunting. The greater the analyst visibility across your environment, the better analysts can detect and respond to malicious activities. Ask vendors about their security integrations and how broadly they can integrate signals from across your IT environment.
pim's MDR, powered by SOPHOS, provides extensive integrations across the full IT stack, including both native and third-party integrations with endpoint, network, cloud, email, and Microsoft 365 technologies. Our approach enables analysts to have broad visibility across the entire customer environment, which in turn elevates threat detection, investigation and response.
Ransomware attacks are as costly as they are common with a suspected attack happening every 11...
The term “cloud” has become so ubiquitous in the past decade that sometimes it is hard to discern...
