As the east coast digs its way out of the most recent snowstorm, now is a great time to discuss how natural disasters can be manipulated by cybercriminals. What better time to exploit the kindness and vulnerability of well-meaning people who just want to help than when there is a natural disaster like a snowstorm, hurricane, or wildfire?

Common Ways Cybercriminals Exploit Natural Disasters
Increase in Malicious Domain Names
During and after weather events and other natural disasters, bad actors often seek to take advantage of people wanting “to help”. They create and register domain names that will encourage you to donate. They will choose domain names that look legitimate and include words like relief, compensation, or charity. Complete with “Donate” buttons, these false domains will trick victims into donating money and worse yet, providing the cybercriminals with their personal financial information. Sometimes these sites can be found through search engines, but most often they are sent through phishing emails.
Rise in Phishing Emails
A phishing scam is a fraudulent email that appears to be a from a legitimate source that asks recipients for money and personal information, such as passwords and credit card numbers. These scammers use an organization’s weakest link, its users, as their entry point.
These fraudulent emails often contain links or attachments that lead to malicious websites. Pay attention to the subject line of natural disaster related emails, attachments, or links. And pay attention to the URLs of any website that is asking for sensitive information or money.
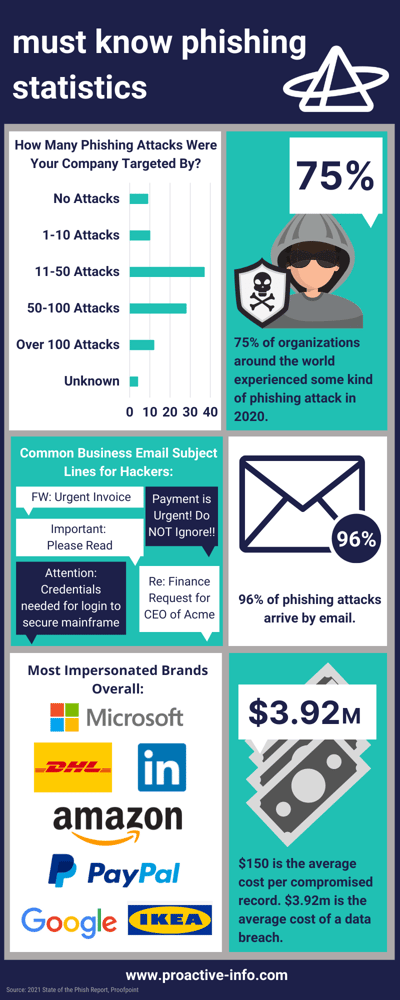
How to Spot the Natural Disaster Phishing Email:
- Be wary of any websites that include the actual name of the natural disaster. For example, www.stormizzyrelief.com.
- Pay attention to the subject line of emails. If they are related to a recent natural disaster like a snow storm or hurricane, be alert and proceed with caution.
- Do NOT open emails containing attachments or links related to recent natural disasters. Even if it looks legitimate. Verify the legitimacy of any email solicitation by contacting the organization directly through a trusted contact number.
- Just like your run of the mill phishing scams, do NOT open links or attachments from unknown sources.
- Stick with donating to well-known charities to avoid being scammed. The American Red Cross is always a safe bet and can point you in the right direction for disaster relief donations.
Review Your Disaster Recovery Plan
Hopefully your business was ready for this natural disaster and its effects with a business continuity plan in place, complete with a well fleshed out disaster recovery plan (DRP). A DRP ensures that all of your systems, data, and personnel are protected.
What is Included in a Disaster Recovery Plan?
- Personnel Roles: Who does what and who is responsible for what in a crisis?
- List of all employees and their contact information
- Major Clients’ contact information
- Record of vital financial relationships
- Inventory of all electronic networks and devices
- An evacuation plan based upon disaster types
- Designation of who oversees restoring your network
- Create a potential purchase list of items needed to resume business operations
- Estimates of disaster recovery times

There is no way to avoid natural disasters from occurring. Nor is there any way for a small business to stop criminals for seeking out ways to exploit people when they are vulnerable. But you can (and should!) train your employees to be on the look out when these disasters occur. Knowing what threats are coming down the pike is a great way to have your defense prepared. Your employees do not have to be your weakest link. If well trained, your employees can be your greatest asset and first line of cybersecurity defense.