While your healthcare organization is focused on providing critical care, improving the lives of your patients, and just being an all-around superhero, hackers and cyber criminals are out there aggressively seeking out your organization’s vulnerabilities and looking for ways to attack. Dealing with highly sensitive data, private personal information, and electronic health records, the healthcare industry is one of the most targeted industries. In fact, the healthcare industry makes up 15% of all cyberattacks, ever proving that cybersecurity and HIPAA compliance remain a constant concern.

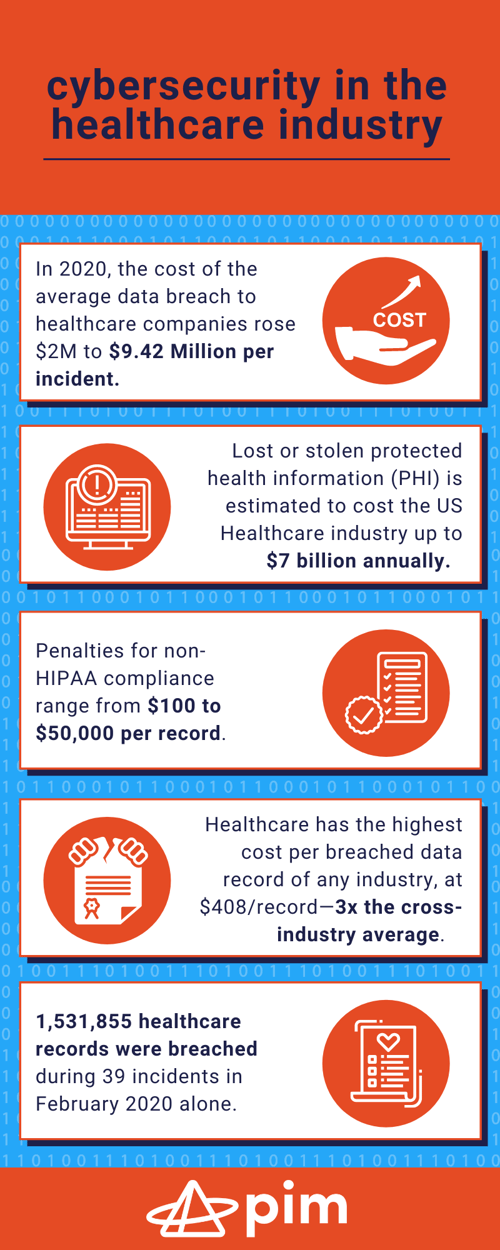
Alarming Stats About Cybersecurity in the Healthcare Industry:
- In 2020, the cost of the average data breach to healthcare companies rose $2M to $9.42 Million per incident. (Source: IBM Security)
- Lost or stolen protected health information (PHI) is estimated to cost the US Healthcare industry up to $7 billion annually. (Source: JAMIA)
- Penalties for non-HIPAA compliance range from $100 to $50,000 per record. (Source: HIPAA Journal)
- Healthcare has the highest cost per breached data record of any industry, at $408/record—3x the cross-industry average. (Source: HIPAA Journal)
- 1,531,855 healthcare records were breached during 39 incidents in February 2020 alone. (Source: HIPAA Journal)
Solutions to Address Common Challenges and Concerns
Unified Communication Tools
Unified Communication (UC) tools with built-in security and data protection along with HIPAA-compliant features allows for properly regulated telehealth programs, using voice, video, recording, and even EMR/HER system integrations.
Enterprise Mobility Management
Enterprise Mobility Management (EMM) solutions give security and visibility into mobile devices, protecting electronic health records (EHR) and sensitive information.
Medical Endpoint Security
Medical endpoint security offers proper ransomware, medical device protection, and patch management.
Bring Your Own Device Policies
Bring Your Own Device (BYOD) policies provide direct guidance on personal device usage and could include “must install” organization’s endpoint security for all employees.
Infrastructure Audits
Infrastructure audits ensure adherence to HIPAA Security Rule Section 164.308(a)(1)(ii) and that networks and physical servers stay protected against unauthorized parties accessing electronic protected health information (PHI).
Ongoing HIPAA Training and Cybersecurity Education
HIPAA and cybersecurity training must be ongoing on not just an “at the time of hire” endeavor. It helps reduce security breaches caused by human error and can help an organization remain in compliance.
Managed Security Services
Managed security services, often provided by managed service providers (MSPs), offer around the clock security handled by experts, remaining in compliance with all regulations and industry requirements and can help a healthcare organization manage threats and recover after breaches.
Network Access Control
Network Access Control (NAC) provides network visibility and access management, enforcing policies across devices and users of corporate/healthcare networks.
Capabilities of network access control include:
Policy Lifecycle Management
Policy lifecycle management enforces policies for all operating scenarios without requiring separate products or additional modules.
Profiling and Visibility
Profiling and visibility recognize block unauthorized profile users and unknown devices before malicious code can wreak havoc on a network.
Guest Networking Access
Manage guests through a customizable, self-service portal that includes guest registration, guest authentication, guest sponsoring, and a guest management portal.
Security Posture Check
A security posture check evaluates security-policy compliance by user type, device type, and operating system.
Incidence Response
Mitigate network threats by enforcing security policies that block, isolate, and repair noncompliant machines without administrator attention.
Bidirectional Integration
Integrate with other security and network solutions through the open/RESTful API.
There are IT Security solutions that are perfect for healthcare. A proper security assessment will help determine your organization’s needs, identify vulnerabilities and provide industry best practice recommendations so that you can continue to focus on what you do best: providing quality healthcare.