Social engineering is a form of cyber manipulation that tricks people into giving up confidential information. Bad actors will target people to gain access to their passwords or banking information, or into networks in order to install malicious software so they can have total access to secure information. These cyber criminals use social engineering tactics because it is easier to convince a person to give up their information than it is to hack a password (unless the password is really weak).

The Vicious Cycle of Social Engineering
Social engineering usually occurs in multiple steps. First the criminal investigates the intended victim to gain necessary background information that might reveal vulnerabilities to be exploited. With this information, often derived from social media profiles, the attacker can attempt to gain the victim’s trust in order to have them reveal sensitive information or grant them access to accounts.
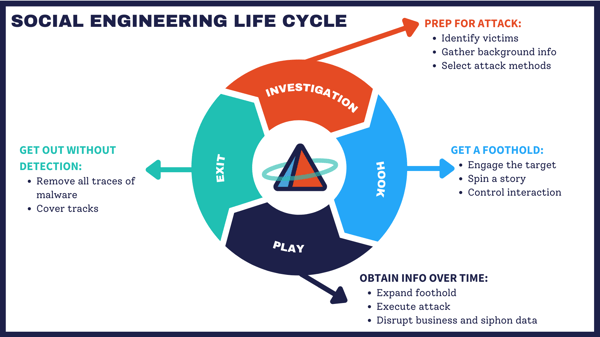
Social engineering takes into account human nature. Therefore, it is important for you and your employees to make sure that they know with whom they communicate and to not share important information with ANYONE. The weakest link in any information security chain is people. Be it from carelessness, inattention, or distraction, a person who cannot discern what emails, websites, or sources are legitimate and trustworthy can be a liability to your organization.
What does a social engineering attack look like?
Social engineering can come in many forms. The one most people know about are phishing scams perpetrated through emails or text messages but they can be carried out anywhere human interaction occurs. The following are the five most common types of social engineering attacks.
Baiting
As its name suggests, baiting involves false promises. If something seems too good to be true, it probably is.
One way baiting is done is by hackers leaving out infected physical media to disperse malware. For example, you’re in the breakroom and see an abandoned thumb drive. It appears to be labeled for your company’s payroll and you are curious. Out of curiosity, you plug it into your work or home computer and BAM! you’ve just installed malware onto your system. The digital version of this is enticing ads that lead to malicious sites that encourage users to download malware infected applications.
Scareware
Scareware involves false alarms and fake threats. Users are led to believe that their systems are ALREADY infected prompting them to install software that is malware. A common scareware example is a legitimate looking popup banner that says “Your computer is infected with harmful spyware programs.” It then offers to install a helpful tool (which is really malware) or will direct you to a malicious site where your computer becomes infected.
Pretexting
In this social engineering tactic, the attacker obtains information through a series of lies. This scam happens when a person pretends to need sensitive information from a would-be victim in order to perform a critical task. They establish trust with the victim by impersonating a co-worker, a government entity, or some other person with authority. The pretexter asks questions that seem to establish a person’s identity but are really a ruse to get the victim’s social security numbers, bank records, addresses, or security passwords.
Phishing
This is by far the most common of all social engineering scams. Phishing scams are emails that create a sense of urgency within their victims and goads them into revealing sensitive information, clicking on links to malicious websites, or opening attachments that contain ransomware.
Spear Phishing
This is a targeted phishing attack wherein an attacker selects specific individuals or organizations. Their message is tailored to the audience in order to appear more genuine. It requires more effort on the part of the cybercriminal, but because of this preparation, are usually more successful. A spear phishing campaign may appear to be coming from a known vendor of an organization and prompt the victims to click on links to change their passwords or credentials, thus giving the attacker access.
Preventing Social Engineering Attacks
Social engineering attacks are geared towards manipulation. If you feel alarmed, fearful, or anxious when receiving an email or message, listen to yourself. Being alert can help you protect yourself and your business from attacks. You should also remember the following strategies to remain vigilant.
- Don’t open emails from unknown or suspicious sources—if you don’t know the sender of an email, you do not need to respond to it.
- Use multifactor authentication—Multifactor authentication helps protect your login information even in the event of a system compromise.
- Keep your antivirus/antimalware software up to date—use automatic updates and scan your system for possible infections.
- When in doubt, check it out. If you are familiar with the alleged sender’s organization but not the person, google the company and track down a legitimate phone number or email address.
Pim offers a phishing campaign wherein your employees can be tested to see if they fall prey to social engineering attempts. After they are tested, you will receive a report with our recommendations. By working together, pim can help you and your company reduce its risk.