Dragnet is deception technology. It is a lightweight, affordable and easy to deploy security token that lures bad actors to fake documents or files embedded into your device. Working as a door chime for your network, it alerts system administrators to when hackers infiltrate your system and where they’ve been snooping.
ProActive is proud to be offering this to not just our clients but to anyone who is wanting to take the additional steps in securing their network and their people. It doesn’t matter if you have one or a hundred and one, the more security you have the more likely you are to catch the incidents quickly, before the damage is done.
SO WHAT IS IT?
- Dragnet is deception technology that acts as an intrusion detection system meant for small and midsize businesses.
- It can detect intrusions into your network, your email, your computer, and more. It can even detect intruders in your cloud storage!
- Dragnet can significantly decrease the time to detect an intrusion, so you can respond quickly to reduce or avoid damages.
- No artificial intelligence, no machine learning, no nonsense. Just simple, reliable security alerts.
HOW DOES IT WORK?
- Dragnet is a new take on an old concept, honeypots. We call them security tokens.
- Security tokens can be in the form of Word documents, PDFs, emails, and more.
- Tokens, sweetened with bait, such as a Word document titled “server passwords.docx” attract hackers to fake documents.
- When a token is accessed, an alarm is set off, alerting security administrators to the presence of the bad actor.
- Admins stop hackers(link blog), fast.
THE PROBLEM DRAGNET IS SOLVING
What is the problem we see in the marketplace regarding cybersecurity? Lots of layers of security but still hackers get in. And the bad hackers linger creating costly chaos and damage. There are options in the market for deception technologies, but the startup entry point is cost prohibitive for most businesses, sometimes costing six figures.
Dragnet minimizes the gaps between detection and action and between the layers of cybersecurity in a manner that is easy and simple.
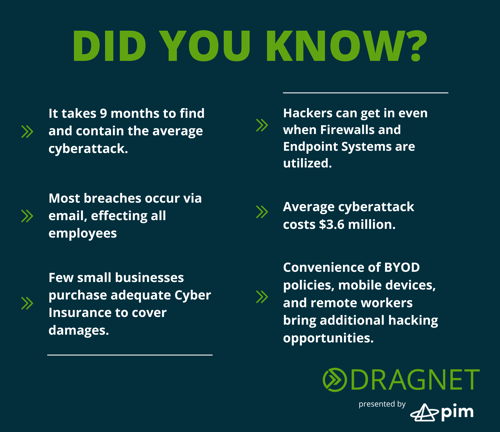
DID YOU KNOW?
- According to IBM, it takes 9 months to find and contain the average cyber-attack?
- Most breaches occur via email, effecting all employees from entry level to C-Suite Executives. No one is immune.
- Few small businesses purchase adequate cyber insurances to cover damages.
- Hackers can get in even when Firewalls and Endpoint Systems are utilized.
- The average cyberattack costs $3.6 million
- The Convenience of BYOD policies, mobile devices, and remote workers brings additional hacking opportunities
